Android warning: Nasty Google Chrome malware lets hackers drain your bank account in seconds

All products are independently selected by our experts. To help us provide free impartial advice, we will earn an affiliate commission if you buy something. Click here to learn more
|GETTY IMAGES

Be alert when updating to the latest version of Chrome
- Security researchers have identified a new threat to millions of Android users
- Known as Brokewell, this new malware strain can empty your bank account
- It also allows hackers to take screenshots and track everything you type
- Malicious software is often disguised as a Google Chrome update
- This tricks Android users into granting permissions for system-wide access
Don't Miss
Most Read
Android users have been cautioned about a new strain of malware that could drain bank accounts in a matter of seconds. Known as Brokewell, hackers often disguise the malicious software as a software update for popular apps, like Google Chrome, to trick Android users into granting it access to permissions.
Once installed, Brokewell can steal sensitive personal information, see everything you type on-screen, take screenshots, read text messages, and even allow hackers to take control of your device.
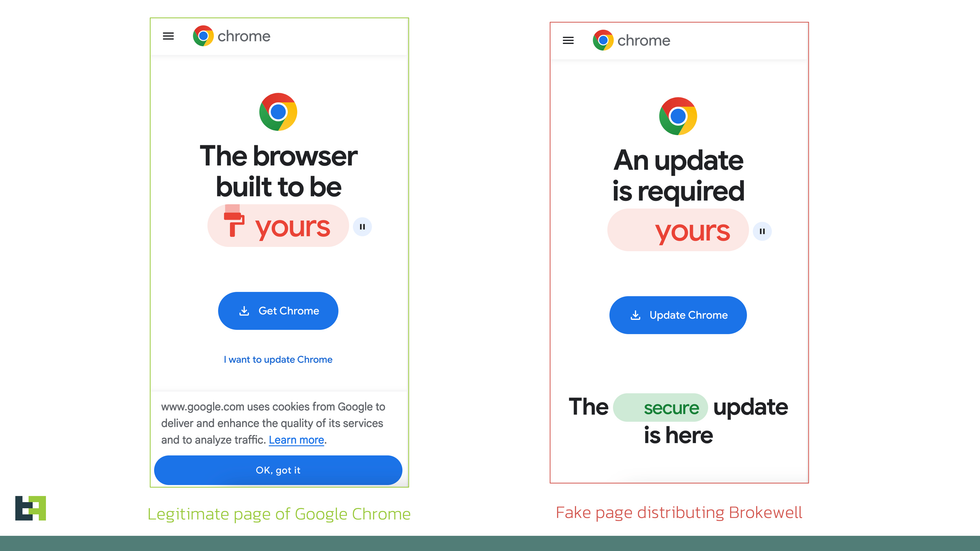
Threat Fabric has shared screenshots of the fraudulent Google Chrome page that tries to tempt people into downloading Brokewell and grant the necessary permissions for that it can wreak havoc on your Android phone and tablet
|THREAT FABRIC
Brokewell is a "significant threat to the banking industry," experts have cautioned.
- View Deal | Get 3 months FREE with Threat Protection from NordVPN
- View Deal | Get 80% antivirus software from Surfshark VPN
- View Deal | Get started with FREE antivirus protection from Malwarebytes
Screenshots published by security specialists Threat Fabric showcase just how difficult it can be to spot the difference between a legitimate website offering access to the latest Google Chrome update and a fraudulent page designed to trick Android users into mistakenly installing Brokewell malware.
Hackers rely on this technique because Android smartphone and tablet owners must grant permissions to Brokewell before it's able to extend its talons into every part of the operating system. Without the right amount of access, it wouldn't be able to steal financial information and track keystrokes.
Brokewell works by overlaying itself on top of everything you do on-screen — allowing it to capture your username and password whenever you log in to a website or app. The malware originates from “a previously unseen malware family with a wide range of capabilities,” Threat Fabric said.
Worse still, Brokewell appears to be in active development, with hackers releasing regular updates to equip the malicious software with new capabilities every day. The malware is being sold alongside a range of other dubious tools via an online retailer, known as Brokewell Cyber Labs.
Experts at Threat Fabric have warned Android users to be on alert for this new strain of malware. To avoid being snared by the malicious software they caution phone and tablet owners to only download updates from official sources, like the Google Play Store.
"We anticipate further evolution of this malware family, as we've already observed almost daily updates to the malware. Brokewell will likely be promoted on underground channels as a rental service, attracting the interest of other cybercriminals and sparking new campaigns targeting different regions," the Dutch cyber security firm warns in its analysis of the recently discovered malware strain.
LATEST DEVELOPMENTS
- Major free Android phone update to be revealed tomorrow
- Windows users on alert as Dell confirms breach for 49 million
- iPad Air refreshed with larger 13-inch screen and new colours
- BT forges ahead with landline switch-off as next 84 locations revealed
"Malware families like Brokewell pose a significant risk for customers of financial institutions, leading to successful fraud cases that are hard to detect without proper fraud detection measures.
"We believe that only a comprehensive, multi-layered fraud detection solution — based on a combination of indicators, including device, behaviour, and identity risks for each customer — can effectively identify and prevent potential fraud from malware families like the newly discovered Brokewell."
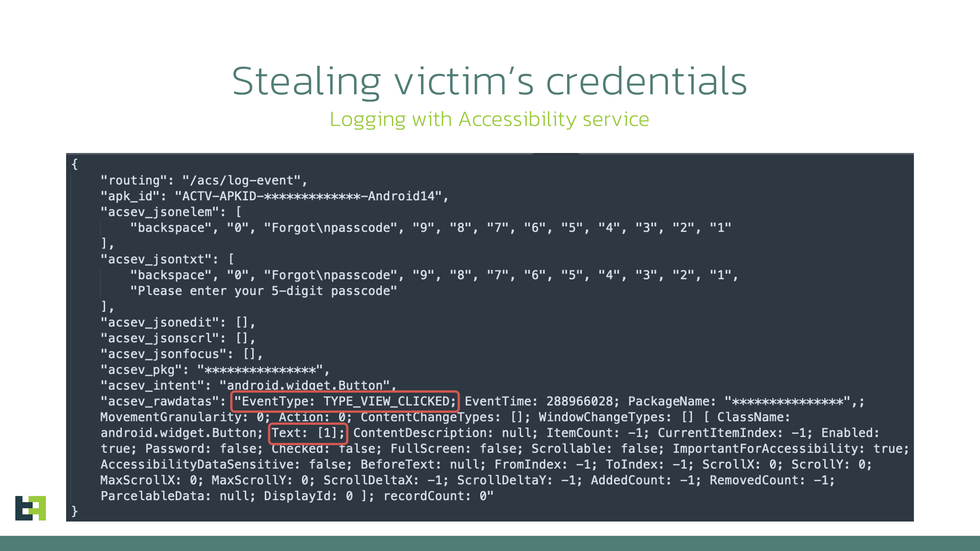
By abusing its system permissions, Brokewell is able to keep tabs on your activity across all apps and websites on your Android phone, including saving login credentials for banking apps and other sensitive software
|THREAT FABRIC
Android users are well accustomed to external threats from hackers. Late last year, researchers at McAfee unearthed a new malware strain, known as Xamalicious, lurking in a series of apps that had passed Google's security checks and were published in the Google Play Store. In February, experts sounded the alarm over 12 dangerous Android apps that could steal your WhatsApp text messages behind your back.
Security experts at the Cyber and Fraud Centre ScotlandCyber and Fraud Centre Scotland have offered some advice to anyone who wants to protect themselves from the latest malware strain terrorising Android users.
- Stick to official app stores — Only download software from trusted sources, like Google Play Store
- Be cautious with software updates — Verify the authenticity of any software update prompts, especially those received outside of the official app store, by checking the app developer’s website
- Review permissions carefully — Pay attention to the permissions that an app requests during installation. Does it seem proportionate for that app? Do not grant unnecessary or overly intrusive permissions
- Use robust mobile security software — Install a reputable antivirus solution to help block malware threats
- Keep your device updated — Always ensure you're running the latest security patches available for Android